The scariest sites on the Net? They're not the ones you might suspect. Here's what to watch for and how to stay safe.
Those photos of Jessica Alba may be murder on your PC. That Google search result that looks as if it answers all your questions may do nothing but create a serious tech headache. The fun you had watching that hilarious video you downloaded may not be worth the misery it can cause your system.

Threat 1 >> Malicious Flash files that can infect your PC
 Adobe's Flash graphics software has become a big malware target in recent years, forcing the company to push out frequent security patches. But another danger you might not know about is associated with Flash cookies. Flash cookies are small bits of data that their creators can use to save Flash-related settings, among other things. But like regular cookies, Flash cookies can track the sites you visit, too. Worse still, when you delete your browser's cookies, Flash cookies get left behind.
Adobe's Flash graphics software has become a big malware target in recent years, forcing the company to push out frequent security patches. But another danger you might not know about is associated with Flash cookies. Flash cookies are small bits of data that their creators can use to save Flash-related settings, among other things. But like regular cookies, Flash cookies can track the sites you visit, too. Worse still, when you delete your browser's cookies, Flash cookies get left behind.
Threat 2 >> Shortened links that lead you to potentially harmful places
 Scammers love Twitter since it relies so much on URL shorteners, services that take long Internet addresses and replace them with something briefer.
Scammers love Twitter since it relies so much on URL shorteners, services that take long Internet addresses and replace them with something briefer.Threat 3 >> E-mail scams or attachments that get you to install malware or give up personal info
The Place: Your e-mail inbox
 Although phishing and infected e-mail attachments are nothing new, the lures that cybercrooks use are constantly evolving, and in some cases they're becoming more difficult to distinguish from legitimate messages. My junk mailbox has a phishing e-mail that looks like a legitimate order confirmation from Amazon. The only hint that something's amiss is the sender's e-mail address.
Although phishing and infected e-mail attachments are nothing new, the lures that cybercrooks use are constantly evolving, and in some cases they're becoming more difficult to distinguish from legitimate messages. My junk mailbox has a phishing e-mail that looks like a legitimate order confirmation from Amazon. The only hint that something's amiss is the sender's e-mail address.
Threat 4 >> Malware hiding in video, music, or software downloads
 Torrent sites (such as BitTorrent) are often used for sharing pirated music, videos, or software, and are a trove of malware. No one vets the download files--they may be malware in disguise.
Torrent sites (such as BitTorrent) are often used for sharing pirated music, videos, or software, and are a trove of malware. No one vets the download files--they may be malware in disguise.
Threat 5 >> Malware in photos or videos of scantily clad women
 Porn sites have a reputation of being less secure than mainstream sites, but that assumption doesn't tell the whole story. "There is no doubt that visiting Websites of ill-repute is deadly dangerous. If you make a habit of it, it's a given that you'll be attacked at some point," says Roger Thompson, chief research officer with security firm AVG. "Unfortunately, staying away from those sites won't keep you safe by itself, because innocent sites get hacked all the time, and are used as lures to draw victims to the attack servers."
Porn sites have a reputation of being less secure than mainstream sites, but that assumption doesn't tell the whole story. "There is no doubt that visiting Websites of ill-repute is deadly dangerous. If you make a habit of it, it's a given that you'll be attacked at some point," says Roger Thompson, chief research officer with security firm AVG. "Unfortunately, staying away from those sites won't keep you safe by itself, because innocent sites get hacked all the time, and are used as lures to draw victims to the attack servers."
Threat 6 >> Trojan horses disguised as video codecs, infecting your PC with malware
 If you watch or download video online, you've likely been told to download a video codec--a small piece of software that provides support for a type of video file--at least once. Usually, these bits of software are perfectly legitimate (for example, the popular DivX codec), but some less-than-reputable download services or video sites may direct you to download a piece of malware disguised as a codec. Security software company Trend Micro provides a good example of what these attacks look like.
If you watch or download video online, you've likely been told to download a video codec--a small piece of software that provides support for a type of video file--at least once. Usually, these bits of software are perfectly legitimate (for example, the popular DivX codec), but some less-than-reputable download services or video sites may direct you to download a piece of malware disguised as a codec. Security software company Trend Micro provides a good example of what these attacks look like.
Threat 7 >> Geolocation--your smartphone and perhaps other parties know where you are
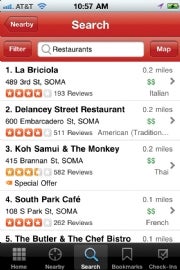
As in this example showing restaurants
in a San Francisco neighborhood,
some smartphone apps, such as Yelp for
iPhone, use your physical location to
provide you with information on nearby
businesses or points of interest. The smartphone market is still in its infancy, really, and so are the threats. One possible concern is the use--or abuse--of geolocation. Although plenty of legitimate uses for location data exist, the potential for inappropriate uses also exists. In one case, a game listed on the Android Market was in reality a client for a spy app. In a less invidious example, a site called pleaserobme.com showed that--for a time--a stream of FourSquare check-ins indicated that a person was away from their home (the site's goal, mind you, wasn't to condone theft, but to raise awareness of the issue).
The smartphone market is still in its infancy, really, and so are the threats. One possible concern is the use--or abuse--of geolocation. Although plenty of legitimate uses for location data exist, the potential for inappropriate uses also exists. In one case, a game listed on the Android Market was in reality a client for a spy app. In a less invidious example, a site called pleaserobme.com showed that--for a time--a stream of FourSquare check-ins indicated that a person was away from their home (the site's goal, mind you, wasn't to condone theft, but to raise awareness of the issue).
The 17 Most Dangerous Places on the Web-P1
Sunday, 3 October 2010 by nkoknki |
0
comments
You've been warned that the Internet is something of a security minefield--that it's easy to get in trouble. You can do everything you can think of to protect yourself and still be taken by a malware infection, a phishing scam, or an invasion of online privacy. We'd like to provide a little help. Here are some of the hazards you may encounter, how dangerous they are, and what you can do to stay out of harm's way.
Not all Web dangers are created equal. Thankfully, our friends at the Department of Homeland Security have made our work of classifying Web threats a little easier. Will you get taken just by visiting that unfamiliar site? Or will you have to look for trouble? Let our threat level indicator be your guide.
The Place: Websites that use Flash
If You Have to Go There: To help protect against Flash-based attacks, make sure you keep your Flash browser plug-ins up-to-date. And you can configure the Flash plug-in to ask you before it downloads any Flash cookies.
The Place: Twitter
And it's very simple to hide malware or scams behind shortened URLs. A shortened link that supposedly points to the latest Internet trend-du-jour may be a Trojan horse in disguise.
If You Have to Go There: Simply don't click links. Of course, that takes some of the fun out of Twitter. The other option is to use a Twitter client app. TweetDeck and Tweetie for Mac have preview features that let you see the full URL before you go to the site in question.
Some link-shortening services, such as Bit.ly, attempt to filter out malicious links, but it seems to be a manual process, not an automatic one. TinyURL has a preview service you can turn on.
If You Have to Go There: Don't trust anything in your inbox. Instead of clicking on links in a retailer's e-mail, go directly to the retailer's site.
The Place: Torrent sites
Ben Edelman, privacy researcher and assistant professor at Harvard Business School, thinks torrent sites are the most dangerous places to visit, since they don't have a business model or reputation to defend (by comparison, many porn sites rely on being deemed trustworthy). "The [torrent] customers, they really don't want to pay," he says.
If You Have to Go There: It's probably best to avoid torrent sites entirely, given their untrustworthy content, but if you must visit, use a secondary PC to protect your main system. Use antivirus software, and keep it updated. Scan downloaded files and wait a couple of days before opening them. Brand-new malware can be tricky to catch, but the delay in opening may allow your antivirus software to get the necessary signatures.
The Place: ‘Legitimate' porn sites
And as mentioned earlier, many porn sites operate as actual, legitimate businesses that want to attract and retain customers. That said, it may be hard to tell the "legit" porn sites from malware-hosting sites that use porn as a lure.
If You Have to Go There: Be suspicious of video downloads, or sites that require you to install video codecs to view videos (see the next threat, below). Using tools like AVG's LinkScanner and McAfee's SiteAdvisor (or SiteAdvisor for Firefox) can help you weed out the malicious sites.
And, again, consider visiting such sites on a secondary machine. You don't want your browser history on the family PC.
The Place: Video download sites, peer-to-peer networks
If You Have to Go There: Your safest option is to stick with well-known video sites such as YouTube and Vimeo. And for catching up on the latest episodes of your favorite TV shows, sites and services like Hulu, TV.com, ABC.com, and iTunes are safer than peer-to-peer networks.
The Place: Your smartphone
Apple recently updated its privacy policy to reflect changes in how it handles location data in iOS 4. The policy now states that "to provide location-based services on Apple products, Apple and our partners and licensees may collect, use and share precise location data." You can read more on Apple's new privacy terms and what they mean for you.
If You Have to Go There: Be particular about the location-based sites, apps, and services that you use. As shown in the screenshot at right services such as Yelp provide good examples of useful location-aware apps. On the other hand, weigh the privacy implications of services like FourSquare or the new Facebook Places feature, and consider how much you feel comfortable divulging. (Read more on how to retain privacy on FourSquare and Facebook Places.)
According Pcworld
Subscribe to:
Post Comments (Atom)


0 comments:
Post a Comment