Threat 8 >> 'Poisoned' search engine results that go to malware-carrying Websites
 Search engine poisoning is the practice of building tainted sites or pages that are designed to rank high in a search on a given topic. For example, according to a recent study by the security firm McAfee, 19 percent of search results for "Cameron Diaz and screensavers" had some sort of malicious payload. Breaking news topics and Facebook are also common search targets for attackers.
Search engine poisoning is the practice of building tainted sites or pages that are designed to rank high in a search on a given topic. For example, according to a recent study by the security firm McAfee, 19 percent of search results for "Cameron Diaz and screensavers" had some sort of malicious payload. Breaking news topics and Facebook are also common search targets for attackers.
Threat 9 >> Malicious PDFs that try to fool you into installing malware
 As Microsoft has become more serious about Windows security over the past few years, would-be attackers have had to find new ways to infect PCs. Attacking flaws in Adobe Acrobat is one of these newer methods. So-called poisoned PDFs are PDF files that have been crafted in such a manner that they trigger bugs in Adobe Reader and Adobe Acrobat; posted on a hijacked Website, they may let an attacker commandeer your PC and access your files and personal info.
As Microsoft has become more serious about Windows security over the past few years, would-be attackers have had to find new ways to infect PCs. Attacking flaws in Adobe Acrobat is one of these newer methods. So-called poisoned PDFs are PDF files that have been crafted in such a manner that they trigger bugs in Adobe Reader and Adobe Acrobat; posted on a hijacked Website, they may let an attacker commandeer your PC and access your files and personal info.
A newer variant takes an otherwise innocent-looking PDF document and inserts malware into it. Adobe Reader may pop up an alert asking if you want to run the malware, but hackers can edit those messages to trick you into opening the file.
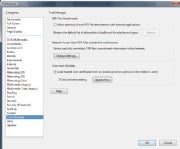
Feeling particularly paranoid?
Uncheck 'Allow opening of non-PDF
file attachments with external
applications' (near the top) to
head off certain PDF exploits
Threat 10 >> Malicious video files using flaws in player software to hijack PCs
 Attackers have been known to exploit flaws in video players such as QuickTime Player and use them to attack PCs. The threats are often "malformed" video files that, like malicious PDFs, trigger bugs in the player software that let the attackers in to spy on you, plant other malware, and more.
Attackers have been known to exploit flaws in video players such as QuickTime Player and use them to attack PCs. The threats are often "malformed" video files that, like malicious PDFs, trigger bugs in the player software that let the attackers in to spy on you, plant other malware, and more.
Threat 11 >> Drive-by downloads that install malware when you visit a site
 A drive-by download occurs when a file downloads and/or installs to your PC without you realizing it. Such downloads can happen just about anywhere. Some sites are built to lure people into a drive-by download; but in a common attack method, criminals will hack a Web page, often on an otherwise legitimate site, and insert code that will download malware to your computer.
A drive-by download occurs when a file downloads and/or installs to your PC without you realizing it. Such downloads can happen just about anywhere. Some sites are built to lure people into a drive-by download; but in a common attack method, criminals will hack a Web page, often on an otherwise legitimate site, and insert code that will download malware to your computer.
Threat 12 >> Fake antivirus software that extorts money--and your credit card information
 Fake antivirus programs look and act like the real thing, complete with alert messages. It isn't until you realize that these alerts are often riddled with typos that you know you're in trouble.
Fake antivirus programs look and act like the real thing, complete with alert messages. It isn't until you realize that these alerts are often riddled with typos that you know you're in trouble.
Threat 13 >> Fraudulent ads on sites that lead you to scams or malware
 Hey--ads aren't all bad! They help sites pay the bills. But cybercriminals have taken out ads on popular sites to lure in victims. Last year, the New York Times site ran an ad from scammers, and earlier this year some less-than-scrupulous companies were gaming Google's Sponsored Links ad program and placing ads that looked like links to major companies' Websites.
Hey--ads aren't all bad! They help sites pay the bills. But cybercriminals have taken out ads on popular sites to lure in victims. Last year, the New York Times site ran an ad from scammers, and earlier this year some less-than-scrupulous companies were gaming Google's Sponsored Links ad program and placing ads that looked like links to major companies' Websites.
Threat 14 >> Questionable Facebook apps
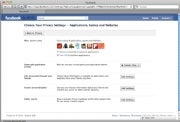
Take a few minutes to check your Facebook
application settings to make sure
that your app privacy settings are
as you want them Facebook apps have long been an issue for security experts. You don't always know who's developing the apps, what they're doing with the data they may be collecting, or the developers' data security practices. Even though you have to approve apps before they can appear on your profile and access your personal information, from there the security of your data is in the developer's hands.
Facebook apps have long been an issue for security experts. You don't always know who's developing the apps, what they're doing with the data they may be collecting, or the developers' data security practices. Even though you have to approve apps before they can appear on your profile and access your personal information, from there the security of your data is in the developer's hands.
Threat 15 >> Sites that lure you in, get you to sign up, then sell your e-mail address for spam
 You've no doubt seen sites around the Web blaring, Get a free iPad! Get a free notebook! A free iPod! It's easy! These sites aren't typically dangerous in the classical sense--you probably won't get infected with malware--but your personal information could be sold to other businesses, who can then use it to sell more stuff to you.
You've no doubt seen sites around the Web blaring, Get a free iPad! Get a free notebook! A free iPod! It's easy! These sites aren't typically dangerous in the classical sense--you probably won't get infected with malware--but your personal information could be sold to other businesses, who can then use it to sell more stuff to you.
Threat 16 >> Phishing 2.0 on social networks that tricks you into downloading malware or giving your Facebook login information to a criminal
 Questionable Facebook apps and malicious shortened links aren't the only dangers lurking on social networks. Sites like Facebook have given rise to new forms of phishing. Scammers might hijack one person's Facebook account, then use it to lure that person's friend into clicking a malicious link, going to spam sites, or giving up their Facebook login information--thereby giving scammers one more Facebook account to hijack.
Questionable Facebook apps and malicious shortened links aren't the only dangers lurking on social networks. Sites like Facebook have given rise to new forms of phishing. Scammers might hijack one person's Facebook account, then use it to lure that person's friend into clicking a malicious link, going to spam sites, or giving up their Facebook login information--thereby giving scammers one more Facebook account to hijack.
Threat 17 >> Oversharing--exposing too much personal information on your social network profiles
 How many times have you seen friends on Facebook or Twitter publicly divulge a bit more information than is necessary? Oversharing isn't just a matter of getting a little too personal--it can leave your private information viewable to the general public. But it's avoidable.
How many times have you seen friends on Facebook or Twitter publicly divulge a bit more information than is necessary? Oversharing isn't just a matter of getting a little too personal--it can leave your private information viewable to the general public. But it's avoidable.
Continue...
Part 1: Threats
The 17 Most Dangerous Places on the Web-P2
Monday, 4 October 2010 by nkoknki |
0
comments
The Place: Search engines
If You Have to Go There: Pick and choose which sites to go to. Don't just blindly click search results; check each URL first to make sure that it really leads to the site you want. Although any site can be hacked, visiting the Washington Post's story on a hot news topic, for example, is probably a wiser choice than following a link to a site you've never heard of before.
The Place: Hacked Websites, plus your inbox
How serious is this problem? In 2009, attacks using malicious PDFs made up 49 percent of Web-based attacks, according to security firm Symantec.
If You Have to Go There: First, always make sure that you're running the latest version of Adobe Reader.
You can also use a different PDF reader, such as Foxit Reader. This can protect you from attacks on holes in Adobe Reader itself, but it won't make you immune to all PDF attacks, such as the newer ones that embed malware inside the PDFs. Make sure, also, that you update to Adobe Reader 9.3.3 or later (Reader 8 users should update to version 8.3.3 or later); these updates change the way Adobe Reader handles non-PDF attachments and reduce the risk from such attacks.
You can turn off Adobe Reader's ability to open non-PDF attachments by going to Preferences, clicking Trust Manager, and unchecking Allow opening of non-PDF file attachments with external applications.
The next major release of Acrobat and Reader will provide a new "protected mode" against these attacks.
The Place: Video download sites
If You Have to Go There: Keep your player software up-to-date. Apple and Microsoft periodically release patches for QuickTime and Windows Media Player, respectively. Avoid downloading videos at random. Stick to well-known video sites such as YouTube, or to download services like iTunes.
The Place: Hacked legitimate sites
If You Have to Go There: The first thing to do is to keep your security software up-to-date, and to run regular malware scans. Many security suites can flag suspicious downloads.
The Place: Your inbox, hacked legitimate sites
Most fake antivirus software is best described as extortionware: The trial version will nag you until you purchase the fake antivirus software-which usually does nothing to protect your PC. Once you send the criminals your credit card information, they can reuse it for other purposes, such as buying a high-priced item under your name.
You can get infected with a fake antivirus app in any number of ways. For example, in drive-by downloads (see the previous item), a malicious payload downloads and installs without the user realizing it or having any time to react.
If You Have to Go There: If you get an alert saying you're infected with malware, but it didn't come from the antivirus software you knowingly installed, stop what you're doing. Try booting into Safe Mode and running a scan using your legitimate antivirus software.
However, such a scan may not clean up all of the malware-either the scanner doesn't have a signature for one fragment, or that piece doesn't act like traditional malware. This may render behavioral detection (which spots malware based on how it acts on your system) useless. If all else fails, you may need to call in a professional.
The Place: Just about any ad-supported Website
"The bad guys have become very clever at exploiting online advertising networks, tricking them into distributing ads that effectively load malicious content--especially nasty, scaremongering pop-ups for rogue antispyware," says Eric Howes, director of research services for security firm GFI Software.
If You Have to Go There: Most large sites, such as PCWorld.com, have ad sales departments that work frequently with a core group of large advertisers, so it's probably safe to click a Microsoft ad on the New York Times site. But as the Google Sponsored Links incident shows, nothing is entirely fail-safe.
The Place: Facebook
.If You Have to Go There: Be selective about the apps you add to your profile--don't take every quiz, for example. Check your privacy settings for Facebook apps, as well: Click the Account drop-down menu in the upper-right corner of Facebook's site, select Privacy Settings, and then click Edit your settings under ‘Applications and Websites'. There, you can control which apps have access to your data, and which of your friends can see what information from apps (such as quiz results); you can also turn off Facebook apps altogether.
The Place: 'Free electronics' sites
If You Have to Go There: Read the privacy policies. And then read them again. Also, beware of privacy policy loopholes--even though a site says that it won't sell your private data to third parties, depending on the language of the policy, they may still be able to give your information to "affiliates."
The Place: Social networks
"One of the bigger dangers currently facing users is malware, adware, and spyware spread through social networks like Facebook and Twitter," says Eric Howes, director of malware research with Sunbelt Software. "Users may receive spam via these networks offering them free deals, links to interesting videos, or even widgets to enhance their Facebook profiles. In many cases what's really being pushed on users is adware, spyware, or even malicious software that can exploit users' PCs."
If You Have to Go There: Don't trust every link posted to Facebook, even if one of your friends posted it. Be especially suspicious if the post is out of the ordinary for that person. Check the person's wall or Twitter @-replies to see if anyone is concerned that the person's account has been compromised.
And if you suspect that your account has been hijacked, change your password immediately. Both Facebook and Twitter have resources to help you keep up-to-date on the latest threats on both sites. Facebook users should visit its security page; if you're on Twitter, be sure to follow @spam and @safety for Twitter security best practices.
The Place: Social networks
"There is a subtle danger that few people understand with the social networking sites, and that is the idea of information leakage," says AVG's Roger Thompson. "People, particularly teens, put all sorts of information online, without realizing that many more people than just their friends can see that data."
Oversharing could very well lead to more serious privacy issues further down the road, Thompson adds. "As today's young teens reach an age to apply for a credit card, I fully expect an onslaught of fraudulent card applications on their behalf, because they unwittingly divulged so much information. Harvesting is going on now, and we have no idea who is doing the harvesting."
If You Have to Go There: This particular threat is relatively easy to avoid, in that a little common sense can go a long way: Just be mindful of what you post. Do you really need to publish your home address and phone number to your Facebook profile?
Finally, be certain to check your privacy settings to make sure that you're not divulging your deepest, darkest secrets to all 500 million Facebook users.
According Pcword
Subscribe to:
Post Comments (Atom)


0 comments:
Post a Comment